Its an interesting question to ponder… What is privacy?
Lets look first at the definition of privacy from Merriam-Webster.com:
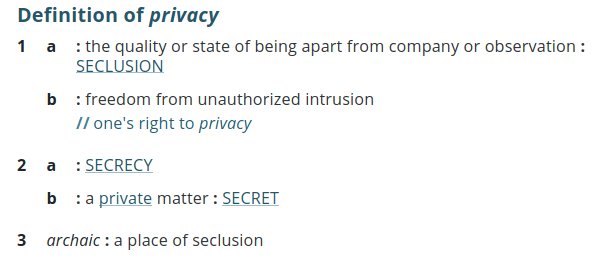
For the purposes of this conversation I believe the important word in that definition is the unauthorized part of “unauthorized intrusion”.
I believe privacy means Choice. It means that you as a human being have the choice on what to share, to whom, and when. I believe this is a fundamental right for every human.
Now this seems to be straight forward, but for some it seems controversial at times. Some people will claim that there is no privacy left in the world, that everything is already ‘out there’, so what is the point? I do not agree with that sentiment, and moreover, I believe that almost everyone has a unrealized and deeply rooted sense of privacy in their daily lives.
We have walls on our houses, we have curtains on our windows, there are doors on the bathrooms. Look at it like this, how many people would utilize a completely glass bathroom in a restaurant, where all patrons would be able to see you conducting restroom activities? Point in fact, there are many comedic videos of this very thing on YouTube, and most people see the glass, and immediately decide to ‘hold it’.
What about publishing the content of your internet browser history, or the texts on your phone, or pictures? Would you be comfortable sharing with the world all the content of your phone? Some people would hand over their phone without hesitation, while others would nervously and protectively slip their phone in their pocket and walk away. I think both sides are okay. You have the choice to share or not.
When privacy is no longer a choice, is when it becomes a problem. I believe that the new privacy legislation in the world is a recognition that a person should have that choice again, and if they decide to share, great… if they decide not to share, that is great as well. While there are a few exceptions, giving people the choice not only protects their rights (and at times their safety), it also shows them respect and dignity as a human being.